Business Ethics In Data Privacy
Posted on: 02 Aug, 2022

Data is the oil of the 21st century. Consumer data has become a valuable asset for businesses, especially for technology firms that involve, the processing of terabytes of data regularly. With the increase in computers, smartphones, smartwatches, cars, social media, and, IoT-based devices, data is collected, stored, and processed every second via internet. Data can be classified into structured and unstructured data, both forms of data are primitive in the business decision process. This helps organizations to understand users’ tastes and preferences so they can provide a curated experience back to users. Since the last decade, there have been major concerns for users regarding how organizations might use their personal data. Many renowned companies indulged in tampering with users’ data for profits. For these issues, many regulations and policies have been taken by the governments at the national and international levels. This study navigates through the abnormal consequences that might arise from unethical activities performed by organizations in mishandling consumers’ data. Also, helps to understand the right ethical data practices to be followed when collecting, maintaining, using, and sharing users’ sensitive data.
What is Data privacy?
Data privacy is the part of data management that deals with taking care of personal data in consistence with data protection laws, guidelines, and general privacy best practices.Data and privacy in brief
Data is the collection of information, statistics, facts, or figures. Personal data is nothing but what is related to an individual living being who can be identified from that data. The concept of data privacy existed some time before the information and technology sector growth. Personal data includes various kinds of information i.e. Health records, Sensitive data, Generic information, Subscriptions, Financial activities, Religious beliefs, Political Opinions, Mobile apps, Mobile Phone GPS, and other biometric data. Collecting these kinds of data is a well-known practice in today’s applications, forms, websites, and operating systems as they help companies with a plethora of information to serve the tailored content to consumers, performing business analysis and research & academics purposes in the organization.Users’ data can be classified into three major groups, namely: Explicit data, implicit data, and, Third-party data. Explicit data means the data that is directly given by the user, which includes preferences, ID’s such as name, email, social accounts, social media posts, contents, billing address, and much more. This explicit data can be gathered by social media applications, surveys, payment portals, shopping platforms, and more. The second group of data is not provided directly by users but collected by companies performing analysis and unconsciously gathering information prior to users’ consent. This includes product functioning, session duration, web activities, location, logs created by system software, and usage activities, especially on smartphones. And at last, the third group consists of information obtained from external parties. This may contain implicit or explicit data or even both, but the data is filtered and offered access by the primary organization. With an ample amount of benefits of collecting personal data, it is crucial to be known about some of the risks and complications involved in using this information. Privacy is the ability to restrict or deny admittance to one’s data. It is very important for organizations to value customers’/users sensitive data. Users have concerns related to their personal data collection specifically for sensitive data, like medical, financial & digital data. While some may not have any issues with certain kinds of data collection, they may be comfortable in sharing their preferences and desire to enhance the recommendations. Some companies trade or allow access to use the data collected from users to generate revenue. Data sharing and utilization beyond the agreement is viewed as a privacy infringement. Proper data management and security involve five vital approaches, the use of the latest and encrypted technology, guidelines and rules for maintaining data, governance and monitoring, welldefined structure, and, procedures for maintenance and sharing of data elements. The data controller is the one responsible for the maintenance and governance of personal data. It’s important to understand the legal charges and abide by the union and federal laws.
Business involved in Data sharing:
Data and analytics developers who share data extrinsically generate 3 times more quantifiable economic benefits than those who don’t. According to the latest Gartner’s chief data officer survey, sharing of data is the key performance indicator of accomplishing powerful partner commitment and giving venture esteem. ‘B2B data sharing’ is the pivotal strategy followed by many organizations in the 21st century. Organizations that engage in B2B data sharing need not provide complete access to their data inventory, only specified datasets can be shared depending on business goals. There are various nosiness models commanding ‘B2B data sharing’: Data Monetization: one-sided approach under which organizations make extra revenue from the information they share with other organizations. Data can also be monetized through the amenities of services. Data Marketplace: trusted intermediaries that bring data providers and data users together to trade in a secured online platform. Industrial Data Platforms: a cooperative and strategic way to deal with the exchange of data among a restricted set of organizations. Open Data Policy: organizations that pick to share information for free to cultivate the development and analysis of new products and/or services. Technical Enablers: Business organizations that are specifically dedicated to enabling data sharing through a specialized technical arrangement. Revenues are acquired from setting up, utilizing, and additionally keeping up with the arrangement.
Government of India bans Chinese apps that present danger to national safety.
In June 2020, the Govt. of India decided to ban around 224 Chinese apps from both the play store and the apple store, including famous applications like Shareit, WeChat, UC browsers, TikTok, Pubg mobile, CamScanner, Mi apps, ES file explorer and more. As per the Ministry of Electronics and information technology, the apps have been known to either run malicious programs or straightforwardly send users’ data to Chinese Data centers without users’ assent. Many of these applications could do reconnaissance and observation exercises through "camera/mic, getting to location data (GPS) and do malicious activities. Center stated that the transition to boycott the applications will defend the interests of crores of Indian versatile and internet users, the assertion said, adding the choice is a designated move to ensure digital wellbeing, security, and sovereignty of Indian cyberspace. After a month, some mirror applications were brought down as they were working regardless of the ban. As they were collecting the most sensitive data such as shopping habits, whereabouts, wellbeing records, social media interactions, texts, and voice chats of the individuals' network of friends, family, and associates.Highlights:
India was one of the key application markets which was growing exponentially well because of low-cost internet services and was a big user base for Chinese tech firms. This ban affected china’s trade relations with India and its ambitious goal of being the ‘Digital superpower of the 21st century’.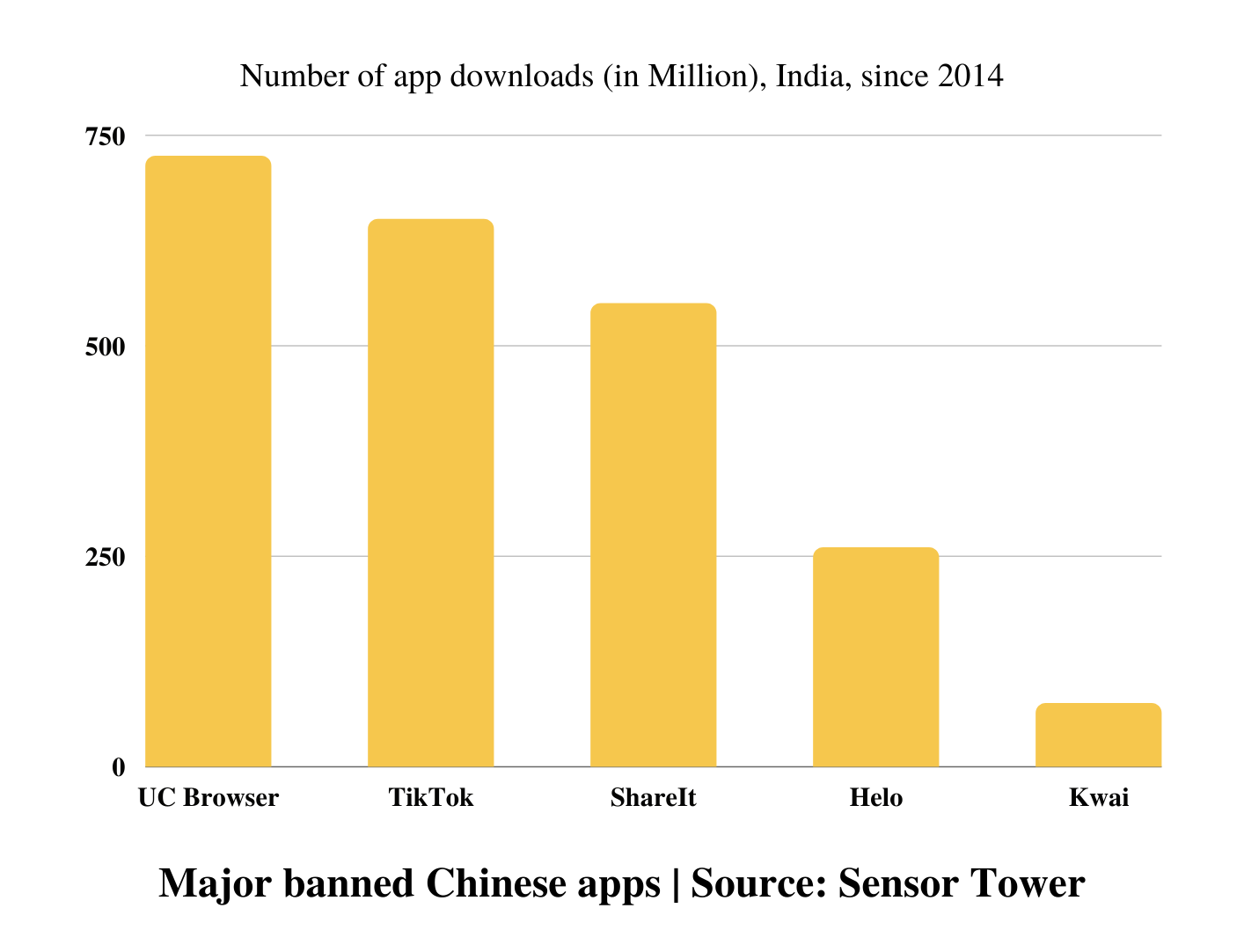
Facebook & Cambridge Analytica Scandal.
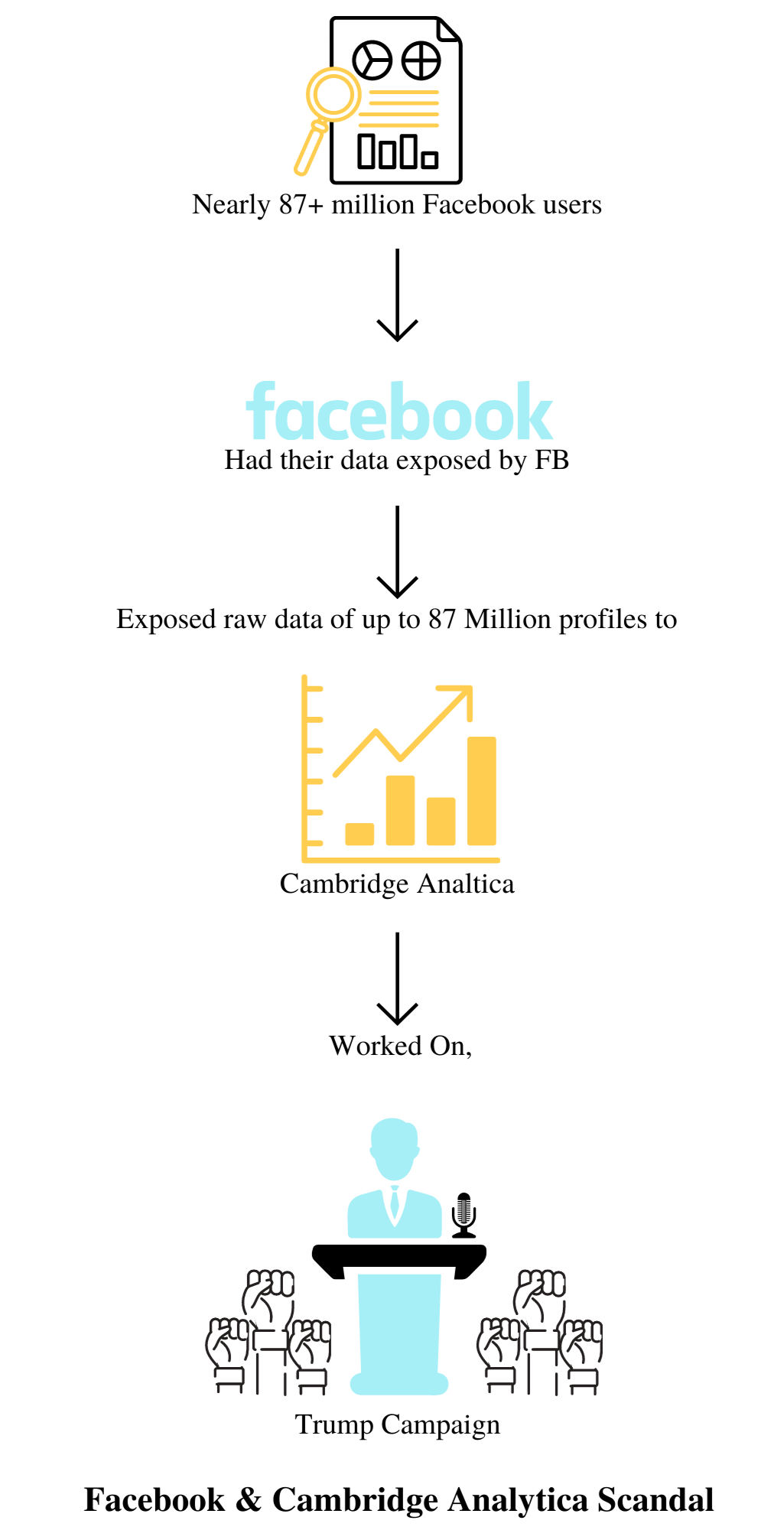
Facebook, one of the world’s largest social media tech giants designed with the goal of connecting humans virtually was involved in a data infringement scandal in March 2018. Facebook was extremely popular by 2018 with about 2.2 billion active monthly users yet the organization's consistent development was defaced by security concerns. Security concerns for Facebook began a long back. Particularly when Facebook launched ‘Open Graph’ API platforms for third-party apps in early 2010. This feature helped external organizations/developers to pull Facebook users’ data and their friends’ data with their single permission. By this, they were able to access personal information like name, sex, location, D.O.B, education, political views, relationship status, religion, text messages, and uploaded media. This was the biggest loophole Facebook failed to understand. In 2018, Facebook was trapped in a significant data breach in which political consulting agency ‘Cambridge Analytica’, drew the sensitive data of more than 87+ million Facebook users without their assent. They used this data with the prime motive of the U.S Presidential campaign, Donald Trump, in the course of the 2016 election. Also, it was found that the information was mishandled to influence the Brexit referendum results in the favor of the Vote Leave campaign. The organization’s response to the scandal was reportedly graceless, defensive, and disoriented. When Facebook learned all about the data breach, it supposedly remained idle and deferred for many months to send notice to Cambridge Analytica to wipe all the data collected. Further, the organization didn't follow up to check whether the illicitly procured information had been wiped out. The scandal put Facebook experiencing the same thing where it was left confronting the wrath of millions of Facebook clients, lawmakers, and sponsors. Further, the organization's share value likewise dropped soon after the news of the data breach came to light. There were several challenges coming up for Facebook, including hate speech and negative campaigns running against it, and claims petitioned for the break of users’ privacy protection. Plus Facebook was fined $ 643,000 by UK’s Information commissioner’s office in October 2018. Company CEO Mark Zuckerberg apologized for the significant ‘breach of trust’ but it was totally not up to the chaos that happened.
Highlights:
As observed by an online survey across America, few Americans trusted Facebook more than other tech giants. Though the company took multiple initiatives and, policies to ward off such data leakages in the future, it lost its reputation among it's user base, there was definitely an erosion of trust.Data privacy measures to be considered by an organization:
The Facebook and Cambridge Analytica incident shows how the abuse of sensitive data can harm business notorieties and trust, so businesses need to question themselves is it really worth taking the risk or if going with compliant data is a more rational choice. Adopting Data protection and privacy policies ensures the enforcement of compliance with mandatory regulatory, internal compliance, legal and ethical requirements along with the need for managing risks. Personal information security can be classified into three parts, specifying clearly the information usage & providing access controls, setting up privacy monitoring units & incident management panels in the organization, and creating privacy awareness among the consumers/users. Businesses must abide by state and federal laws of their respective nations such as the ‘General Protection Regulation’ (GDPR) in the European Union, ‘The Bureau of Indian Standards’ (BIS) & Information Technology Act in India, California Consumers Privacy Act (CCPA) in the US and other respective nations laws which gives people more control over the personal data that business accumulates about them. Also, these regulations provide supervision on the implementation of the laws.
In the final analysis,
Safeguarding data today is a full-time job today the very least. Security practices that are effective one day can be outdated the next, ensuring both updated physical and digital infrastructures is foremost necessary. While moral utilization of data is a regular effort, realizing that personal data subjects’ safety and rights are flawless is worth of work. Seeing privacy from the point of view of ethics can help businesses lay out and work on their code of conduct. Also, allows organizations to make meaningful decisions and grow in the competitive world.References
1) Canterbury Christ Church University, “Data Protection in Research”.
2) Venky anant, Lisa Donchak, James Kaplan, and Henning Soller, “The consumer-data opportunity and the privacy imperative” available in: www.mckinsley.com/risk
3) Understanding Data Privacy and How to Build a Data Privacy Compliance Program Hyperproof.io
4) Akansha barua, “Ban on Chinese apps in India” available in: www.jetir.org (ISSN2349-5162)
5) Raquel Pita Guerreiro Marcelino Duarte, “Facebook in face of crisis”.
6) Article: Facebook sued over Cambridge Analytica data scandal.
7) The Facebook and Cambridge Analytica scandal, explained with a simple diagram.